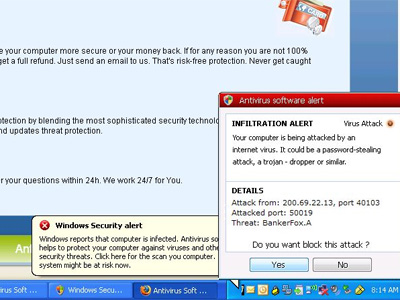
There are reports around the Twin Cities today that the Star Tribune’s Web site has spent the morning serving up malware to its visitors. First reports surfaced from the University of St. Thomas earlier today. Since then, a growing number of people surveyed via Twitter also report problems. Your local public radio station blogger also had viruses showing up after visiting and commenting on a review of last night’s B.B. King concert.
A few minutes later, a program made to look like anti-virus software popped up reporting the computer was under attack, but the “program” itself was a virus.
The Star Tribune posted this notice a few minutes ago:
We have received reports that a third-party advertising network has been placing a “Malware Ad” onto our site.
A “Malware Ad” is a potentially malicious ad that could contain a virus or attempt to get you to pay for unsolicited services. The ad informs you that your machine has been infected with a virus and that you should click it to run a scan on your machine. We do not approve of this ad and consider it a potential security threat to your computer — although we do not yet know that for certain.
We take this situation very seriously and are responding aggressively to get it resolved. We have removed all ad networks from our site. All advertising networks will be required to perform complete a check of every ad they run, and to verify that they are not running this ad, before we allow them to run on our site.
If you see an ad matching this description, please let us know about it by emailing content@startribune.com.
How does something like this happen? Ask the New York Times. It happened to the newspaper’s Web site last fall.
While Web site owners usually review the ads they run for quality control and security reasons, many online ads are sold and distributed through middlemen known as ad networks. As a result, ads can appear on a site that its operators have not directly approved, and they may be pulled into its pages from computer servers that it does not control.
About half of the ads delivered to The Times’s Web site come from ad networks. As reports of strange activity came in over the weekend, the technical and advertising staff at The Times began to suspect that a rogue ad had slipped through this way, and they moved to stop displaying such ads, said Diane McNulty, a spokeswoman for the Times Company.
But it now appears that the ad was approved by the site’s advertising operations team, Ms. McNulty said. People visiting nytimes.com continued to complain about the pop-up ads throughout the weekend.
The real damage, however, comes when the employee sheepishly delivers his infected laptop to his company’s I.T. department, fruitlessly claiming he didn’t spend the weekend visiting porn sites.
For the record: It’s not uncommon for Web sites to use third-party ad servers. Jeff Harkness of MPR’s digital unit reports that MPR “(1) allows our clients to serve ads to our sites via 3rd party networks (Doubleclick, Mediaplex and EyeWonder are among the more common) and (2) National Public Media has an ad network that we partner with.
But you’re safe here. Trust me.
Update 3:23 p.m. – So now that you’ve got an infected computer, how can you get rid of the Star Tribune’s malware/virus. This page has a step-by-step instruction. It’s not easy. (Alternately, you can try these instructions at Bleeping Computer.)
